Title: IDOR in Cookies section
Description of the Vulnerability: This website has an IDOR vulnerability in the cookies section.
Summary: In the picoCTF Logon challenge, we were able to access the flag by changing the values of the cookie admin from false to true in the cookie section and getting all the privileges of an admin.
The technical investigation finished at 8:40 UTC, concluding that there was no malicious intent or indicators of exploitation.
Steps to reproduce:
1. Click on the link to the Logon website.
2. Type the name in the username section (except Joe) and press enter.
3. You will be logged in as the website is checking the password only for the user Joe.
4. Inspect the page and go to the Cookies section under Application.
5. Change the value from False to True in the column besides Admin.
6. Refresh the page.
7. PicoCTF Flag will be in front of you.
Impact:
1. Got access to admin privileges by changing the values in the cookie section.
Mitigation:
1. Do not give access to the client side.
2. Don't trust user inputs.
3. Store cookies in an encrypted format.
POC (Proof of concept):




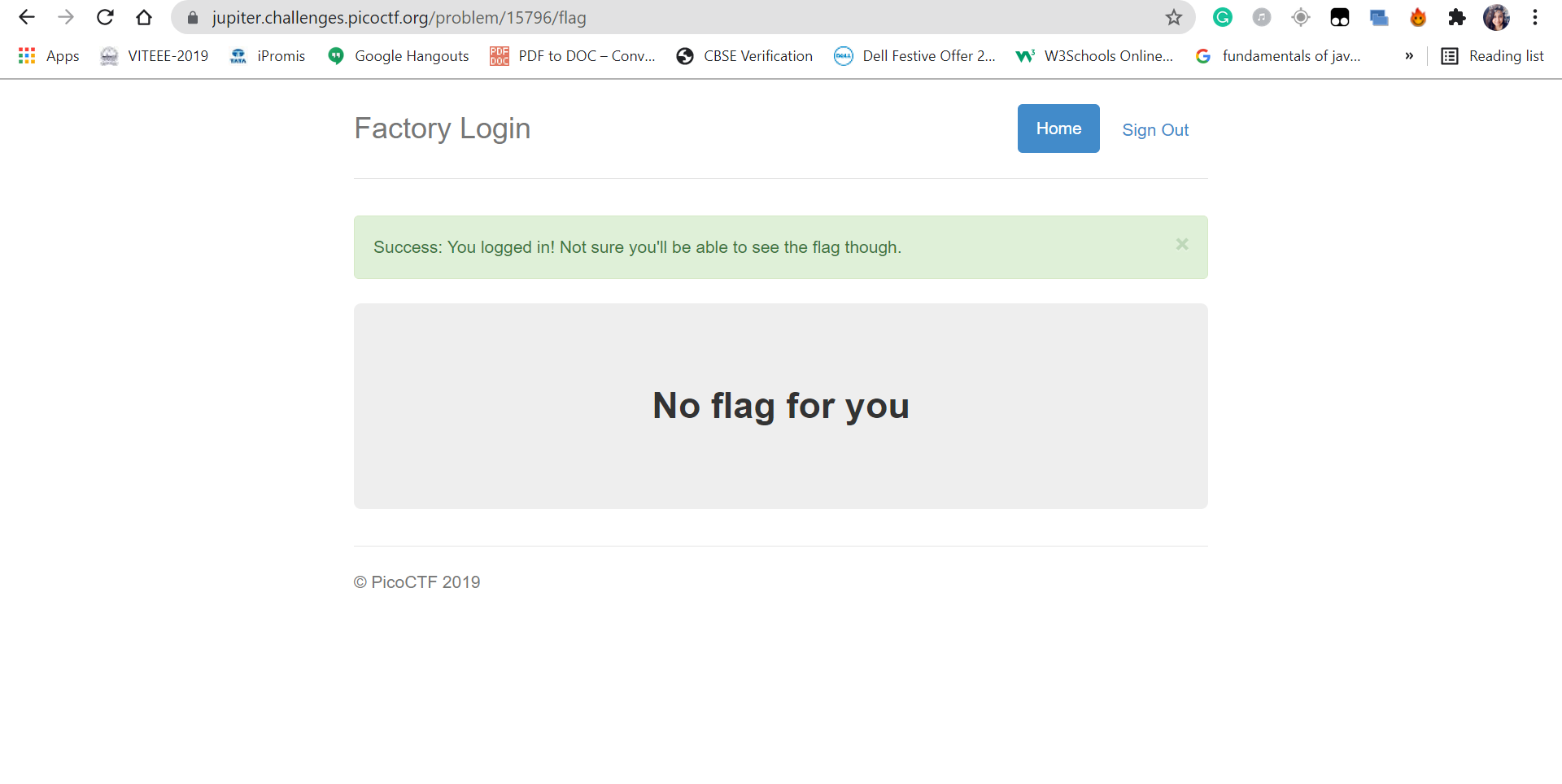
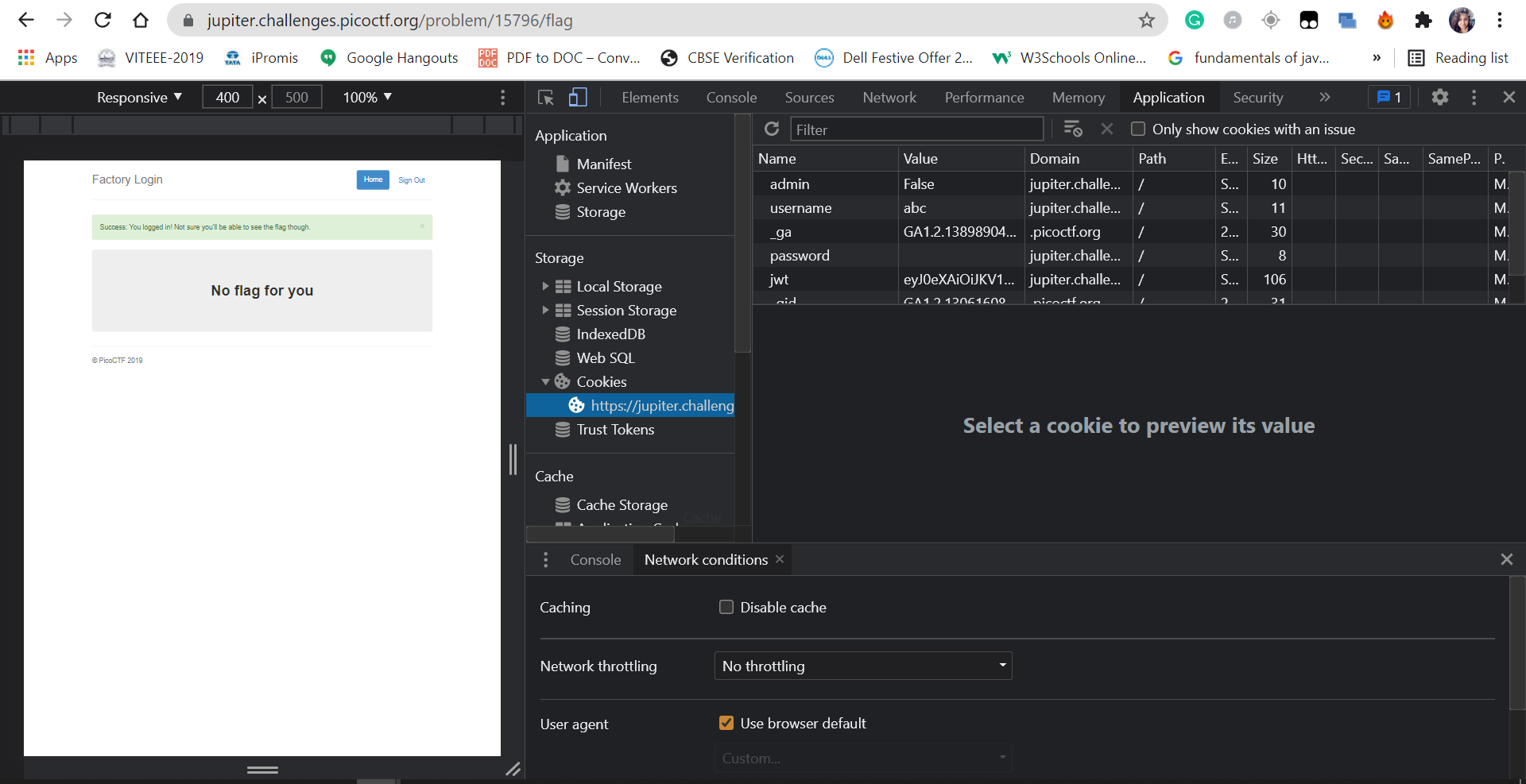


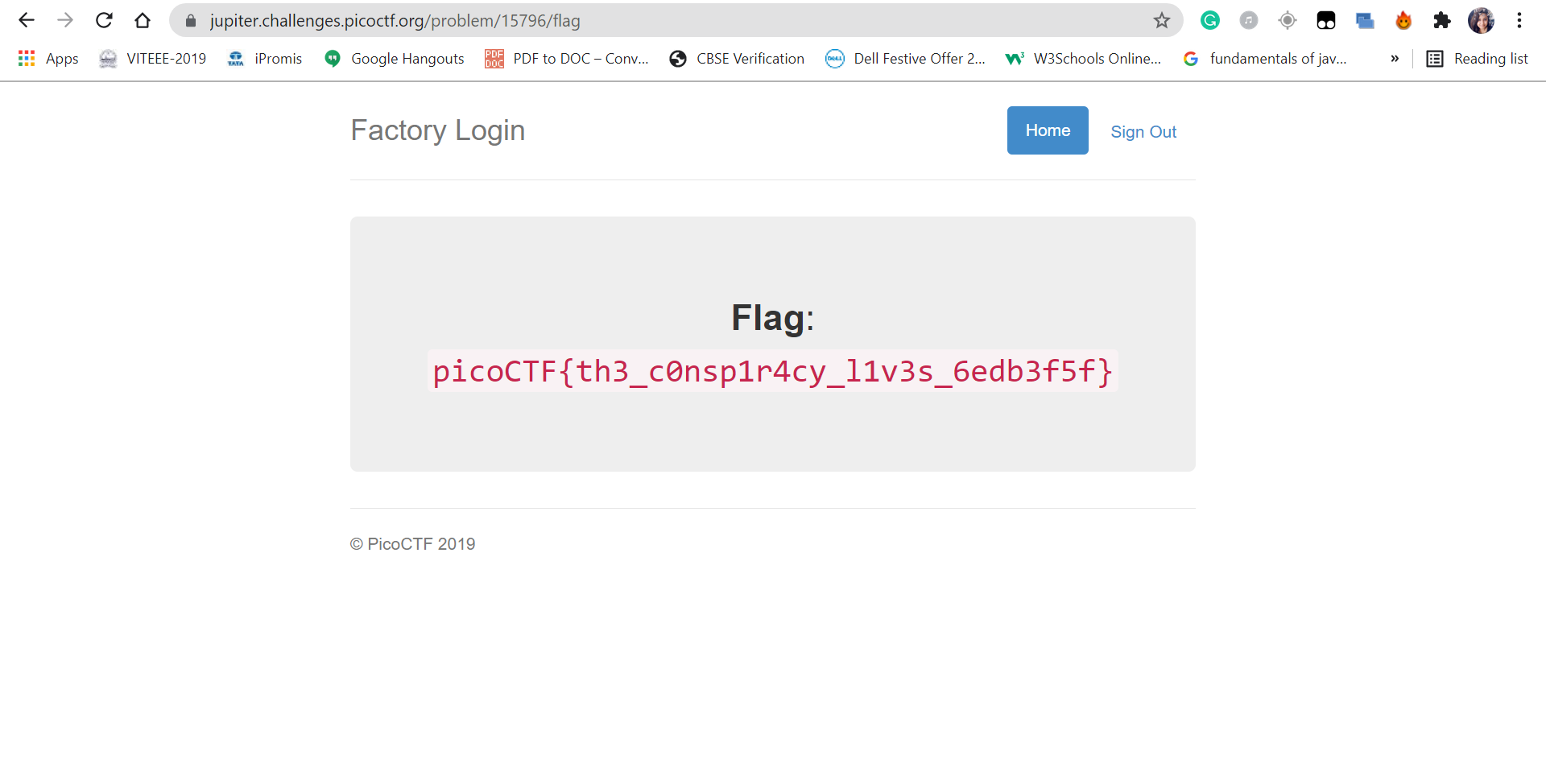
0 Response to "Vulnerability Assessment Penetration Test Report for Logon (Category Web Exploitation - picoCTF)"
Post a Comment
If you have any doubts, please let me know...